Well what happens is that in my previous post like jumping
firewalls using OpenSSH as they did not say when the proxy was we were going to skip authentication, as is the case of the university proxy, if use for example the client that comes with the OpenSSH for Windows NEVER going to get through that proxy knows nothing and will always try to direct connection, then pans. [NOTE:] I have realized that putting OpenSSH to serve for the 443 is better than it used by 80 because some ISPs block port 80 (as I do with ETB) but port 443 is blocked by ISPs or by the firewalls, since it is the HTTPS port.)
Well, for this example we need:
A relay team set outside the firewall (see previous post
The client putty
 Well, then, we know that we have configured relay team to accept SSH connections through a port accessible through the firewall, in this case we say that the port is 443.
Well, then, we know that we have configured relay team to accept SSH connections through a port accessible through the firewall, in this case we say that the port is 443. For this example I will show how to play on the server of Lineage 2 of
TehGamers,
I will assume you already have installed and configured the client and already have your hosts file in the folder and it works fine (this the computer is going to play, relay team does not need to have the client installed or modified hosts file).
Well, the first thing we need is information on which port the client connects to Lineage II, this information is online, but do not have to go further: 2106 to the authentication server 7777
for
game server 2009 for the game server
guard 80 is also connected to authentication
- So now we know what ports to release, now comes the tricky part is making all the tweaks we need for this to work, so let's start: The first thing to do is modify the hosts file on the computer where we play (that which is inside the firewall and have installed the client) The server hosts file TehGamers look something like this:
- # Tehgamers patch
91.185.193.200 l2patcher.lineage2.com
216.107.250.194 nProtect.lineage2.com
- What we need then is to redirect those connections to localhost, for modify the file like this:
# Address modified for the port forwarding: 127.0.0.1 l2authd.lineage2.com
127.0.0.1 l2patcher.lineage2.com
127.0.0.1 nProtect.lineage2.com# 91.185.193.200 l2patcher.lineage2.com
# Tehgamers patch
edited this three lines ...
# 91.185.193.200 l2authd.lineage2.com
# 216.107.250.194 nProtect.lineage2.com
Note that all I did was comment on the original lines server and add three new all pointing to localhost, the reason for this is that when you want to play again outside the firewall as the commented lines and invest now.
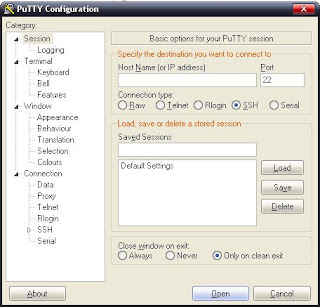
Now need to configure Putty to do the port forwarding, open putty and the first thing we see is this:
Here we introduce the necessary fields in Hostname (or IP Address) introduce the team relay ip or domain that points to it and Port as the port you're using (the 443 in my case). The next thing you do is go to Connection -> Proxy on the left, the window displays the following:
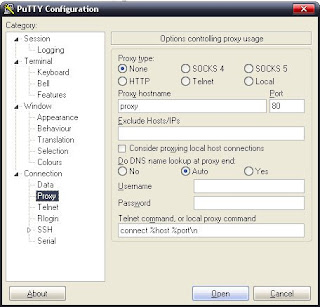
Here we enter the proxy information, then I think there is much to explain, but for example in If the university is: HTTP proxy is so select that option in Proxy Type, then in the proxy address as: proxy.unal.edu.co, the following is the port which is 8080. Ready, all that remains is to put the user name and password of the SIA and already, we will set up Putty to go through the University proxy that requires authentication.
Not so hard right?
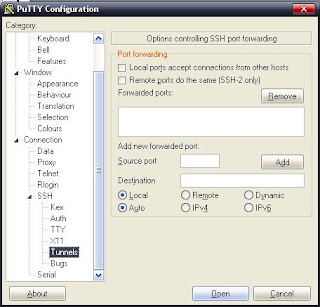
[NOTE:] If you are concerned that recording is played Lineage within the university in the proxy do not worry, SSH connections are encrypted with 128 bits, so there is no danger, the only thing they encrypted packets will be going to the 443 (a port that is normal to flow encrypted information). Well, now there Set the forwarding: that we do in Connection -> SSH -> Tunnels:
Here we add each of the ports to which forwarding can we do, we must have regard to the hosts file , then:
2106 for the port that goes to the authentication server, the redirection is: Source port: 2106, Destination: 91.185.193.200:2106
for port 7777 going to the game server, the redirection is : Source port: 7777, Destination: 91.185.193.200:7777
 For port 2009 that will guard the game server, the redirection is: Source port: 2009 Destination: 216.107.250.194:2009
For port 2009 that will guard the game server, the redirection is: Source port: 2009 Destination: 216.107.250.194:2009 to port 80 going to the authentication server redirection is: Source port: 80 Destination: 91.185.193.200:80
What is being done here is to tell the Putty that everything between the local computer ( which lie inside the firewall) on port 2106 forwarded it to the port 91,185,193,200 in 2106 making use of the relay team, and so with the rest of the ports. Note that I put the IP addresses instead of hostnames, the reason for this is that the relay team does not have the Hosts file, if any could have used the names of the hosts.
 When all tunnels are ready simply to give
When all tunnels are ready simply to give Open
to putty. Ready
, if we do a netstat-n-a-p TCP-b see among other entries:
TCP 127.0.0.1:7777
 0.0.0.0:0 LISTENING 3852
0.0.0.0:0 LISTENING 3852 [putty.exe ]
- TCP 127.0.0.1:2106
- 0.0.0.0:0 LISTENING 3852
- [putty.exe]
TCP 127.0.0.1:2009
0.0.0.0:0 LISTENING 3852
[putty.exe]
TCP 127.0.0.1:80
0.0.0.0:0 LISTENING 3852Packets: Sent = 4, Received = 4, Lost = 0
[putty.exe]
netstat These entries confirm that the forwarding is done, now we must prove that it addresses are being treated by our own team, for this we ping the hosts file addresses:
Pinging l2authd.lineage2.com [127.0.0.1] with 32 bytes of data:
Reply from 127.0.0.1: bytes = 32 time Reply from 127.0.0.1: bytes = 32 time
Answer from 127.0.0.1: bytes = 32 time
Reply from 127.0.0.1: bytes = 32 time Ping statistics for 127.0.0.1:
(0% loss),
Approximate round trip times in milliseconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
<1m ttl="128" If all are answered by localhost (resolve to 127.0.0.1) then we are ready, AHRA if we open the Lineage and fun.
<1m ttl="128"
[NOTE:] This really does not work, after having authenticated with the auth server that tells the client what IP address is the game server to which you are connecting, so that client never does a DNS Lookup to locate the game server and therefore no way to trick you into connecting to localhost. So, when you try to make the connection through the proxy dies. <1m ttl="128"
<1m ttl="128" To do so would be to use a technique called ip-forwarding to conciste to trick the system to send packages that are a certain address to another, I am investigating the asusnto but have not achieved anything for Windows at least. Anyway, I leave the post so they know how to jump the Firewall with proxy authentication.
0 comments:
Post a Comment